One of my all-time favorite podcasts is Gimlet Media’s Reply All (definitely check it out if you haven’t already). Last week’s episode was called, What Kind of Idiot Gets Phished? In a quest to figure out just how easy it is to get phished, the show host pulls off a pretty epic prank on her boss by hiring a pro to hack his email. The hacker bought the domain name “gimletrnedia.com” (which looks super similar to Gimlet’s actual domain name, “gimletmedia.com” — can you see the difference?) and sent what appeared to be an email from a Gimlet employee with an attachment to download. The boss took the bait, and boom, the hacker had access to his email.
One of my all-time favorite podcasts is Gimlet Media’s Reply All (definitely check it out if you haven’t already). Last week’s episode was called, What Kind of Idiot Gets Phished? In a quest to figure out just how easy it is to get phished, the show host pulls off a pretty epic prank on her boss by hiring a pro to hack his email. The hacker bought the domain name “gimletrnedia.com” (which looks super similar to Gimlet’s actual domain name, “gimletmedia.com” — can you see the difference?) and sent what appeared to be an email from a Gimlet employee with an attachment to download. The boss took the bait, and boom, the hacker had access to his email.
As a lawyer and a developer, I’d like to think that I’m above phishing schemes, but I almost clicked a phishing link today! The email looked like it was coming from our web host, BlueHost, related to our antifirm.com domain. Take a look below — can you spot the red flag?
20170418135616_001 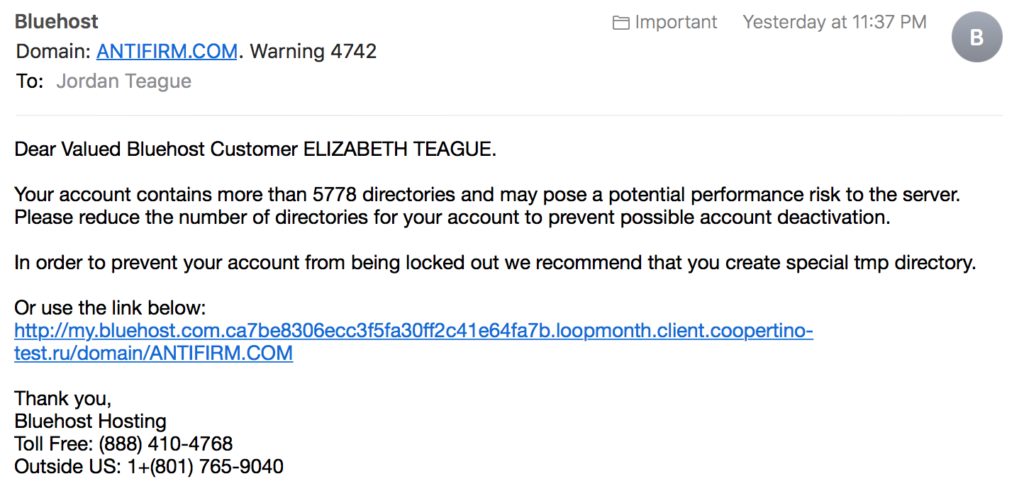
It took me a minute, but on closer inspection, the link isn’t to bluehost.com at all. It’s to a website hosted at coopertino-test.ru. I Googled that domain and confirmed that I almost got hacked. The other red flag to me was the statement that our website has 5778 directories. Since I’m our web host, I happened to know that shouldn’t be true.
Lawyers are generally a smart bunch, but they aren’t immune to phishing. Law firms get phished all the time, putting their own data and their client’s confidences at risk. If you run a law firm, how can you make sure your employees street-wise about phishing? As a starting point, phish them! Like the Reply All host did, hire some pros to hack your employees. It’ll give you an idea of how vulnerable your firm is to attacks and help you form a game plan for training and prevention.